Thursday☕️

Economics & Markets:
- Yesterday’s U.S. stock market:

- Yesterday’s commodity market:
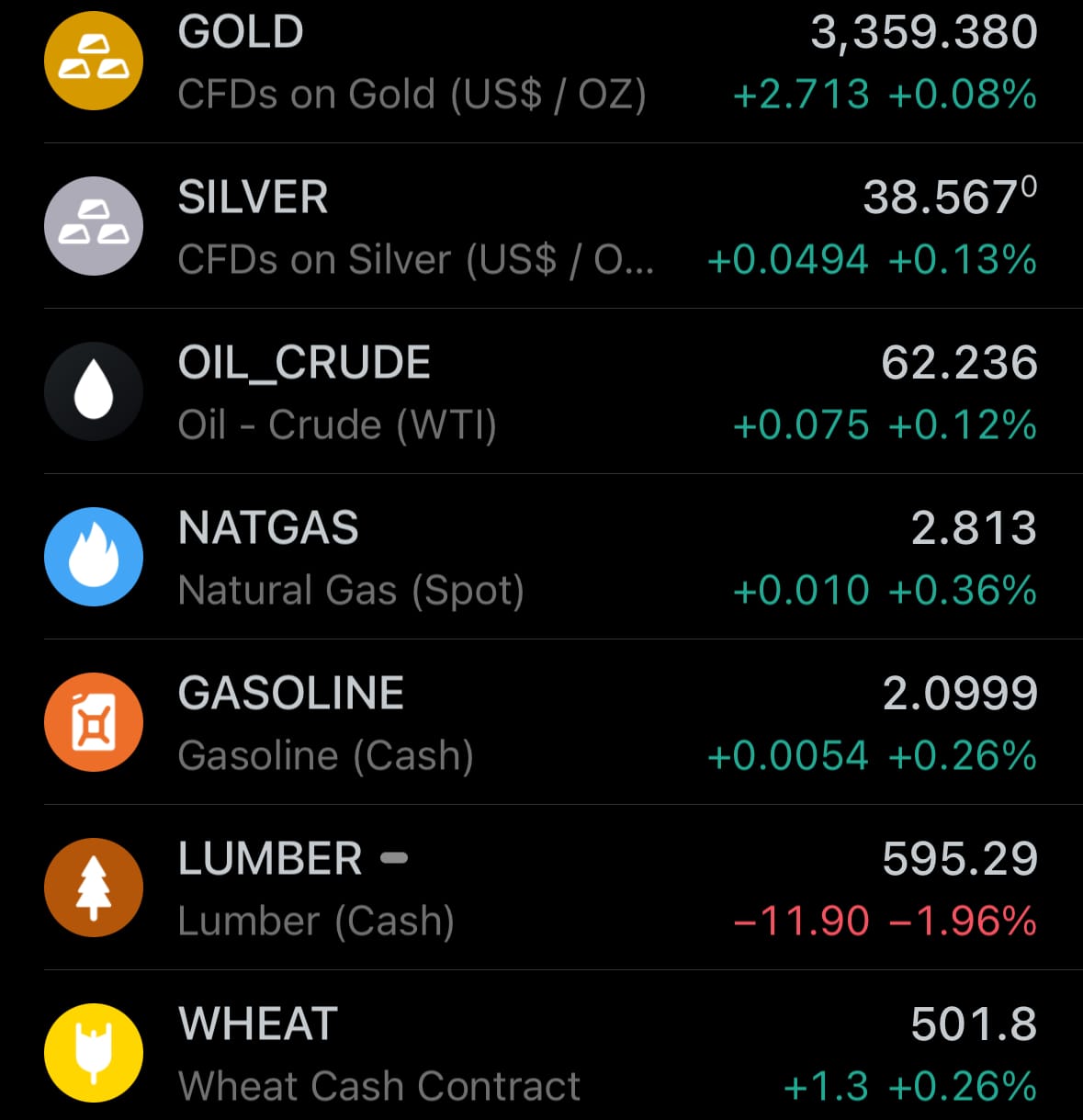
- Yesterday’s crypto market:
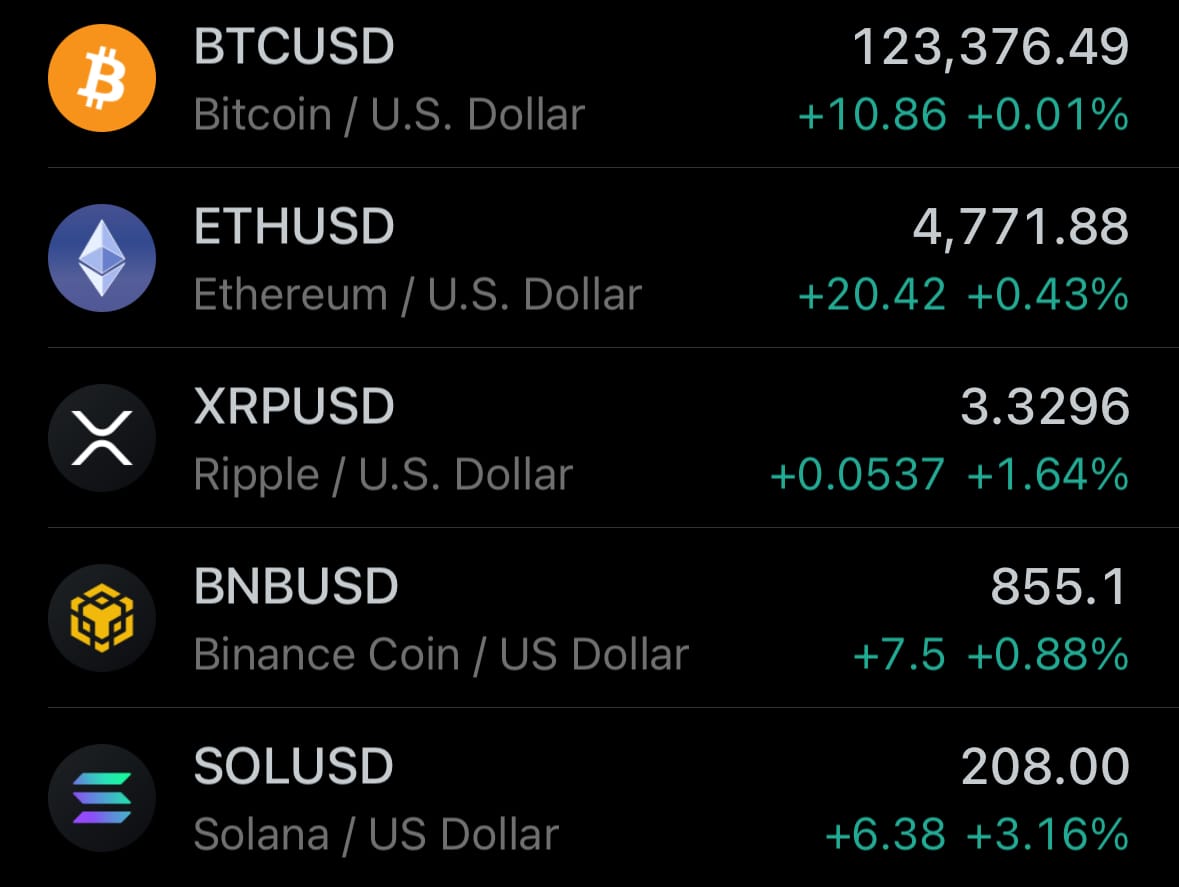
Geopolitics & Military Activity:
- As of August 14, 2025, preparations are underway for a high-stakes summit between U.S. President Donald Trump and Russian President Vladimir Putin, scheduled for August 15 at Joint Base Elmendorf-Richardson, a military installation in Anchorage, Alaska. The meeting aims to address the ongoing war in Ukraine, with Trump emphasizing the need for Russia to cease hostilities and warning of severe consequences, potentially including economic sanctions, if no progress is made toward a ceasefire or peace deal. Discussions may involve territorial concessions, with Trump expressing intentions to negotiate the return of some Ukrainian land held by Russia, while Putin has maintained a firm stance against unilateral withdrawals. The choice of Alaska as the venue underscores its strategic significance near Russian borders, amid broader U.S. efforts to involve European leaders and Ukrainian President Volodymyr Zelenskyy in follow-up talks to ensure inclusive negotiations.
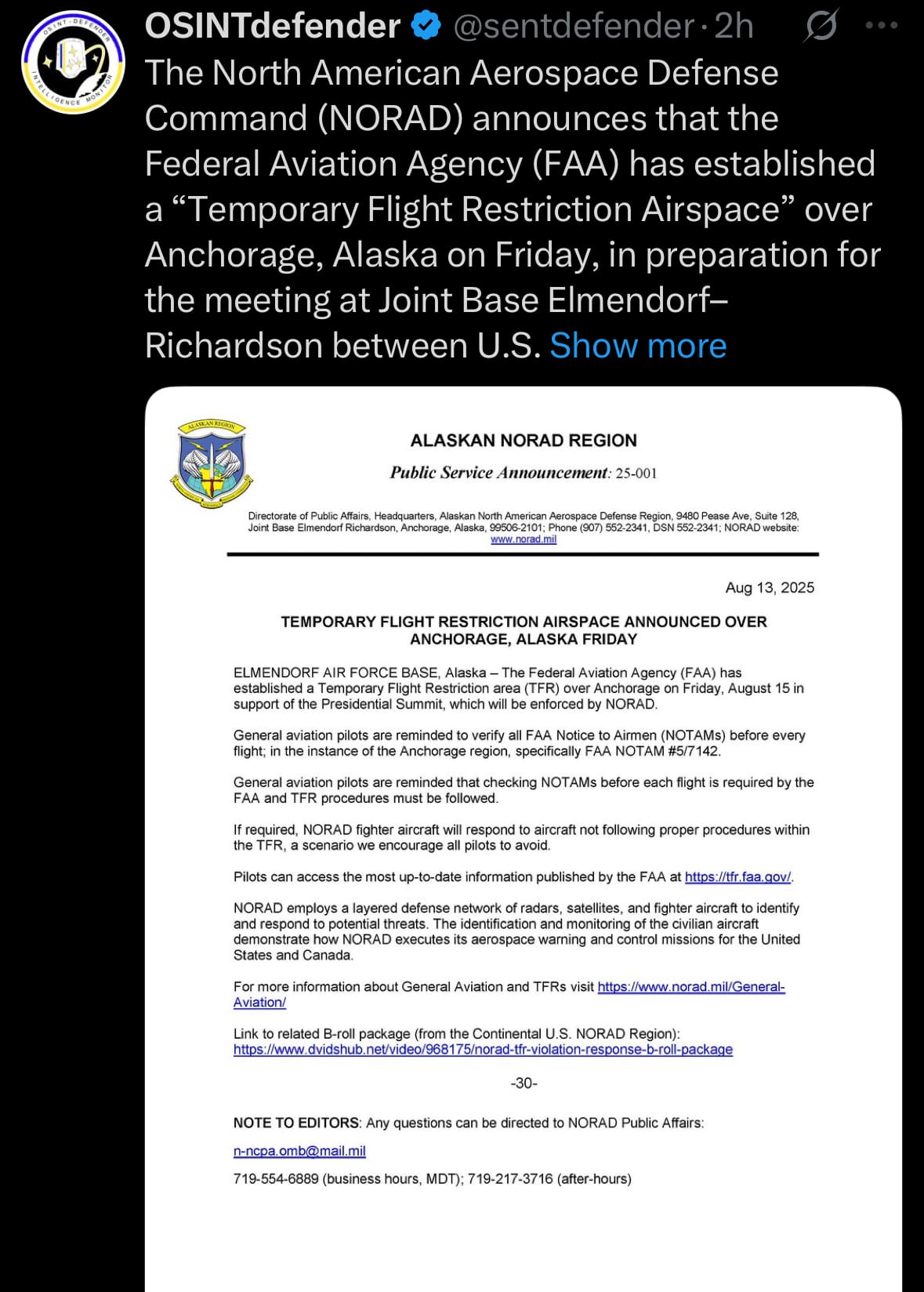
- In response to the summit, the North American Aerospace Defense Command (NORAD), a binational U.S.-Canadian organization responsible for aerospace warning, control, and maritime defense of North America, has coordinated with the Federal Aviation Administration (FAA) to implement a Temporary Flight Restriction (TFR) over Anchorage from August 15 to 16. This airspace restriction prohibits unauthorized aircraft from entering a designated zone up to 17,999 feet altitude to ensure security during the high-profile event, mitigating risks from potential threats like drones or unauthorized flights. Enforcement involves NORAD's monitoring through radar and fighter jet intercepts, FAA notifications to pilots via Notices to Airmen (NOTAMs), and potential penalties including fines or aircraft interception for violations, reflecting standard protocols for protecting VIP gatherings and sensitive military sites.
Environment & Weather:
- On August 14 Typhoon Yagi is positioned inland over southern China at approximately 24.4°N, 115.7°E, having downgraded to a tropical storm after making landfall in Guangdong province early on August 14, following its initial crossing of southern Taiwan on August 13 with sustained winds up to 191 km/h (Category 2 equivalent) and rainfall exceeding 500 mm in mountainous areas. The storm continues to bring heavy rains and gusty winds as it weakens while moving further inland, with forecasts warning of ongoing risks for flash floods, landslides, and disruptions in affected regions of Guangdong and potentially neighboring provinces like Fujian.
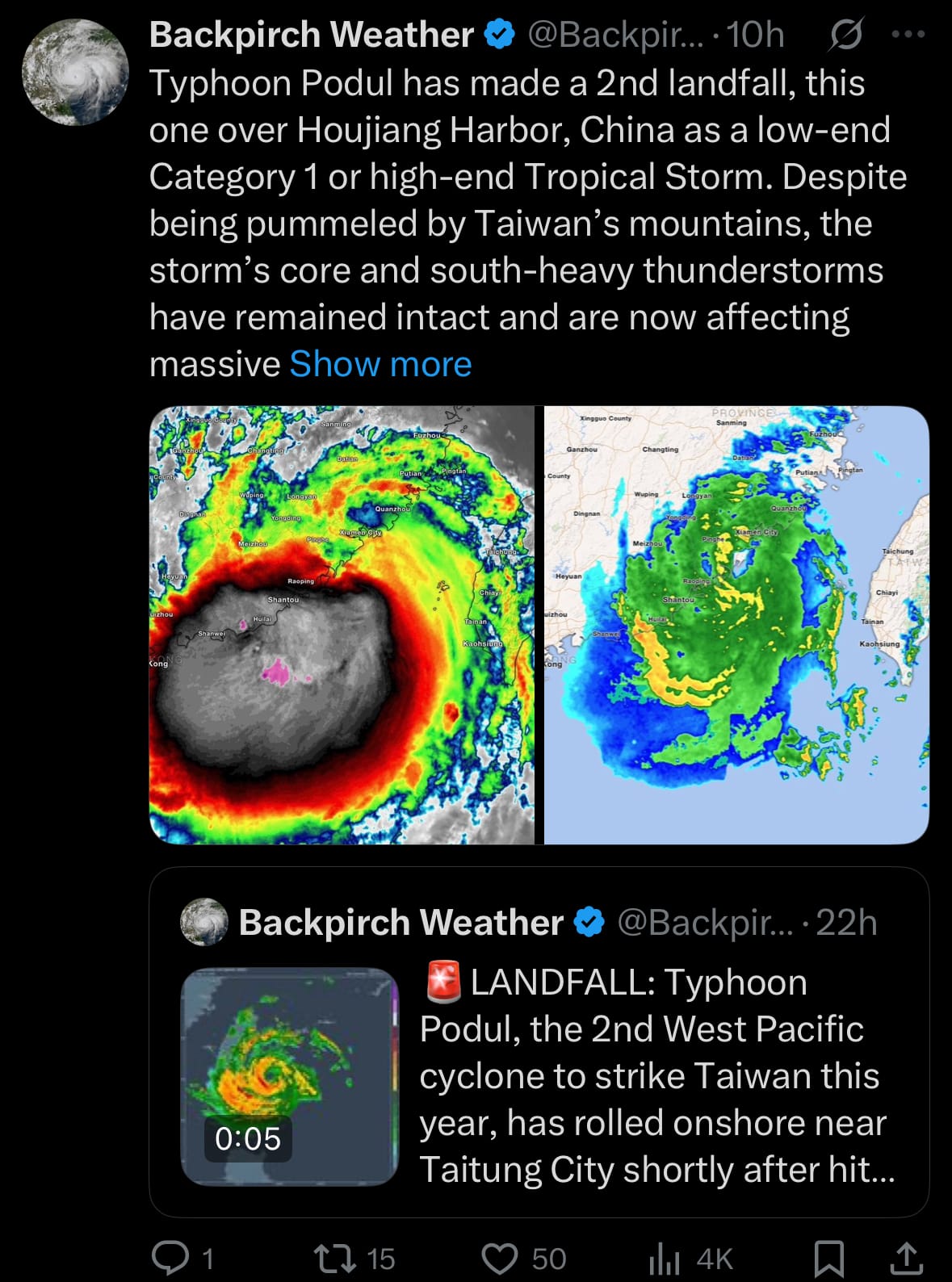
- Damage in Taiwan includes one person reported missing, at least 33 injuries, over 7,300 evacuations from high-risk areas, and power outages affecting more than 134,500 households due to flooding and downed lines, alongside localized flooding, fallen trees, minor landslides in Taitung and eastern counties, hundreds of flight cancellations, and closures of schools and offices in nine cities and counties. In China, initial reports indicate emerging impacts from the landfall, including heavy rainfall triggering floods and strong winds causing disruptions, with authorities reporting preliminary evacuations, power interruptions, and minor structural damage in coastal Guangdong areas, though comprehensive assessments are ongoing as the storm progresses inland.
Space:
- On August 13, 2025, a space launch took place from the Wenchang Space Launch Site in Hainan Province, China, deploying the eighth batch of low Earth orbit satellites for the Guowang megaconstellation project, also referred to as SatNet. This initiative aims to build a network of up to 13,000 satellites to provide global broadband internet services, with the mission carrying approximately 10 communication satellites focused on delivering low-latency connectivity, especially to remote and underserved regions. The launch vehicle used was the Long March-5B carrier rocket, augmented by a Yuanzheng-2 upper stage, representing the 588th mission in the Long March rocket series and showcasing capabilities in heavy-lift and orbital insertion technologies.
- The operation was carried out by the China Aerospace Science and Technology Corporation (CASC), a state-owned entity managed under the China National Space Administration (CNSA), which oversees China's space activities. All satellites reached their intended orbits successfully, with no anomalies reported, marking this as the fourth such deployment in less than three weeks and contributing to the expansion of satellite-based infrastructure. Official accounts noted no immediate concerns regarding debris or other issues, while the project aligns with broader efforts in satellite telecommunications amid global conversations on managing orbital space and frequency resources.
Statistic:
- Largest assets on Earth by market capitalization:
- Gold: $22.864T
- 🇺🇸 NVIDIA: $4.428T
- 🇺🇸 Microsoft: $3.869T
- 🇺🇸 Apple: $3.462T
- Bitcoin: $2.459T
- 🇺🇸 Alphabet (Google): $2.450T
- 🇺🇸 Amazon: $2.394T
- Silver: $2.174T
- 🇺🇸 Meta Platforms: $1.959T
- 🇸🇦 Saudi Aramco: $1.550T
- 🇺🇸 Broadcom: $1.453T
- 🇹🇼 TSMC: $1.252T
- 🇺🇸 Tesla: $1.094T
- 🇺🇸 Berkshire Hathaway: $1.029T
- 🇺🇸 Walmart: $805.94B
- 🇺🇸 JPMorgan Chase: $798.88B
- 🇨🇳 Tencent: $699.37B
- 🇺🇸 Oracle: $685.86B
- 🇺🇸 Visa: $664.86B
- 🇺🇸 Eli Lilly: $592.10B
- SPY: $591.86B
- Ethereum: $575.48B
- 🇺🇸 Mastercard: $522.42B
- 🇺🇸 Netflix: $511.79B
- 🇺🇸 Exxon Mobil: $458.72B
- 🇺🇸 Palantir: $437.38B
History:
- Cryptography, the art and science of secure communication, has roots stretching back thousands of years. Early forms, such as the Egyptian hieroglyphic substitutions and the Spartan scytale, relied on simple transpositions and substitutions to conceal messages. The classical era saw the emergence of the Caesar cipher, which shifted letters by a fixed number, and more sophisticated polyalphabetic ciphers like the Vigenère cipher during the Renaissance. By the 19th and early 20th centuries, mechanical cipher machines, most famously the German Enigma during World War II, represented a leap forward in complexity, with encryption relying on intricate rotor mechanisms. The Allied cryptanalysis efforts at Bletchley Park, led by figures like Alan Turing, showcased how mathematical rigor and computation could break even advanced ciphers of the era.
- In the late 20th century, cryptography shifted from a primarily military and diplomatic tool to a cornerstone of global digital communication. The advent of public-key cryptography in the 1970s, pioneered by systems like RSA, enabled secure key exchange over untrusted channels and fueled the growth of e-commerce and internet security. Symmetric algorithms like AES and asymmetric systems like elliptic curve cryptography became standard for protecting sensitive data. Today, as quantum computing threatens to render many classical algorithms vulnerable through Shor’s algorithm, research is accelerating into quantum-resistant (post-quantum) encryption schemes. At the same time, quantum key distribution (QKD) offers a new paradigm—leveraging quantum mechanics to ensure communication security in ways theoretically immune to interception, marking the next frontier in the millennia-long evolution of cryptography.
Image of the day:

Thanks for reading!
Earth is complicated, we make it simple.
Click image to view the Earth Intelligence System:


Support/Suggestions Email:
earthintelligence@earthintel.news




