Wednesday☕️

Trending:
- On February 3, 2026, Mexico and the United States reached an agreement on annual minimum water deliveries from the Rio Grande (Río Bravo) under the 1944 Water Treaty. Mexico committed to delivering a minimum of 350,000 acre-feet (about 432 million cubic meters) per year to the U.S. on average over a five-year cycle, with flexibility to adjust for drought conditions but strict enforcement of the overall obligation.
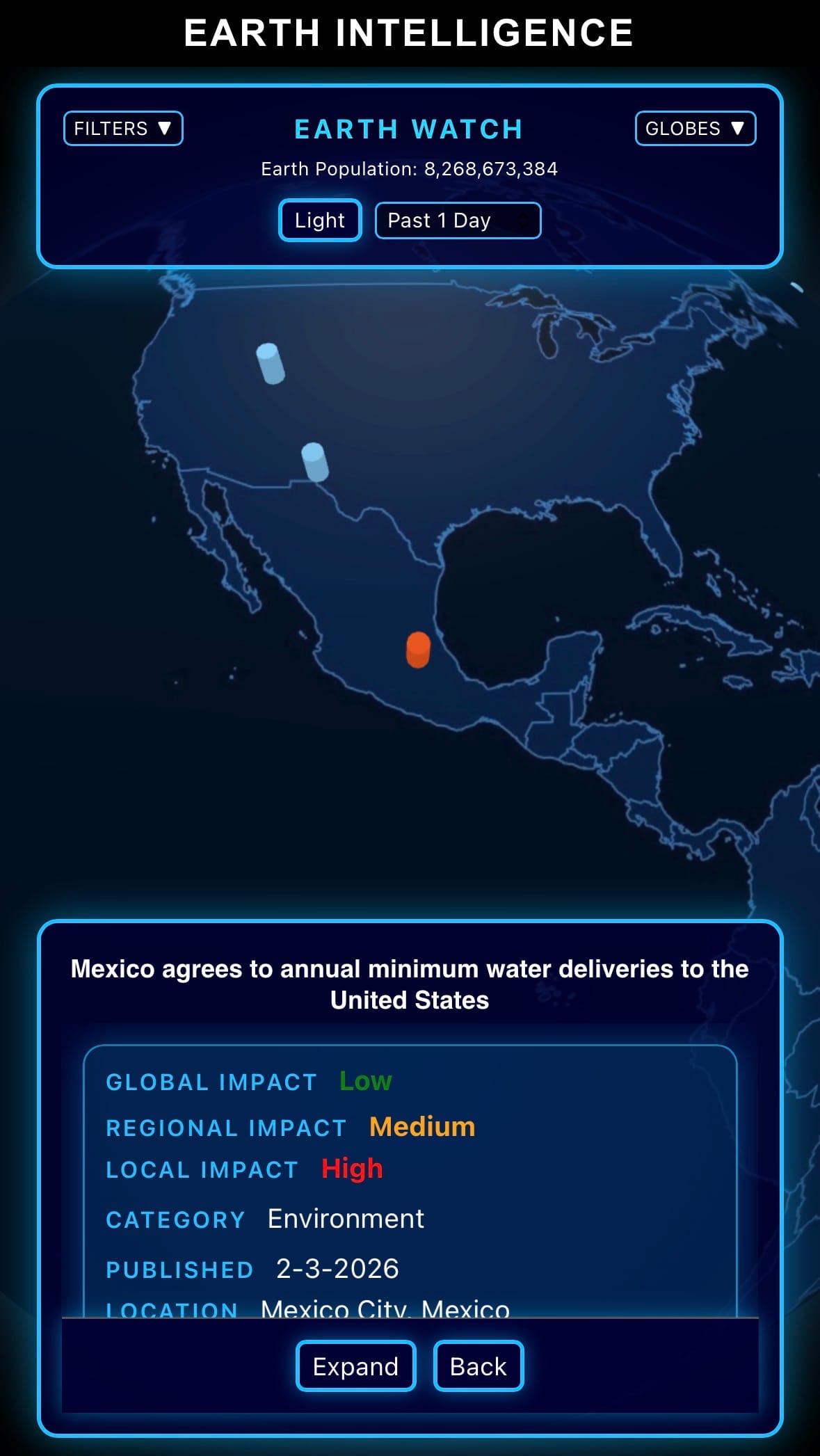
- The deal resolves long-standing U.S. complaints about Mexico's chronic shortfalls in delivering its allotted share from the Rio Grande, which had led to tensions, congressional hearings, and threats of trade penalties. Under the new terms, Mexico will prioritize deliveries to the U.S. from its reservoirs (such as Falcon and Amistad) and improve infrastructure monitoring and transparency. The agreement includes provisions for joint drought management and data sharing to prevent future disputes.
Economics & Markets:
- Yesterday’s U.S. stock market:

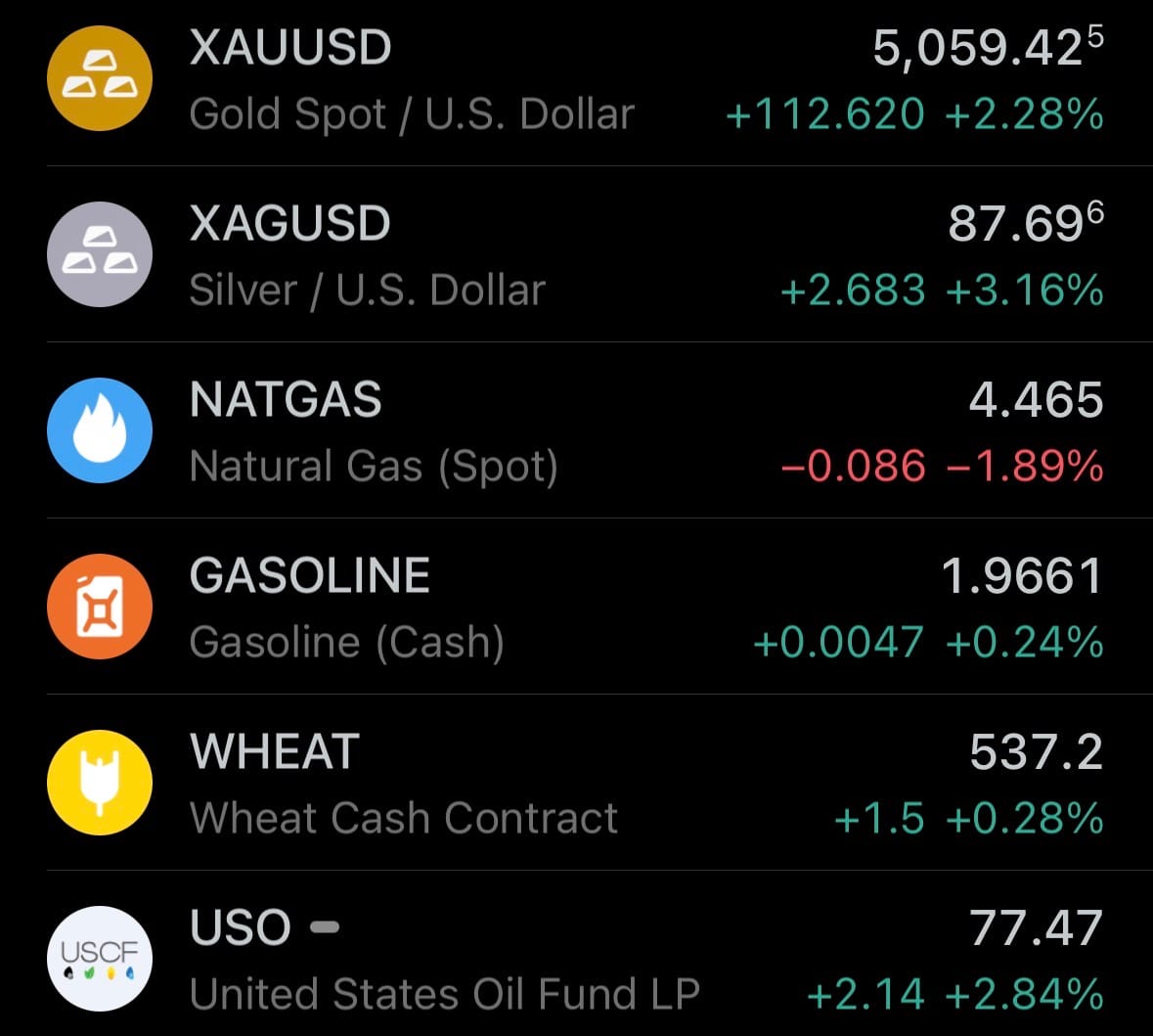
- Yesterday’s commodity market:
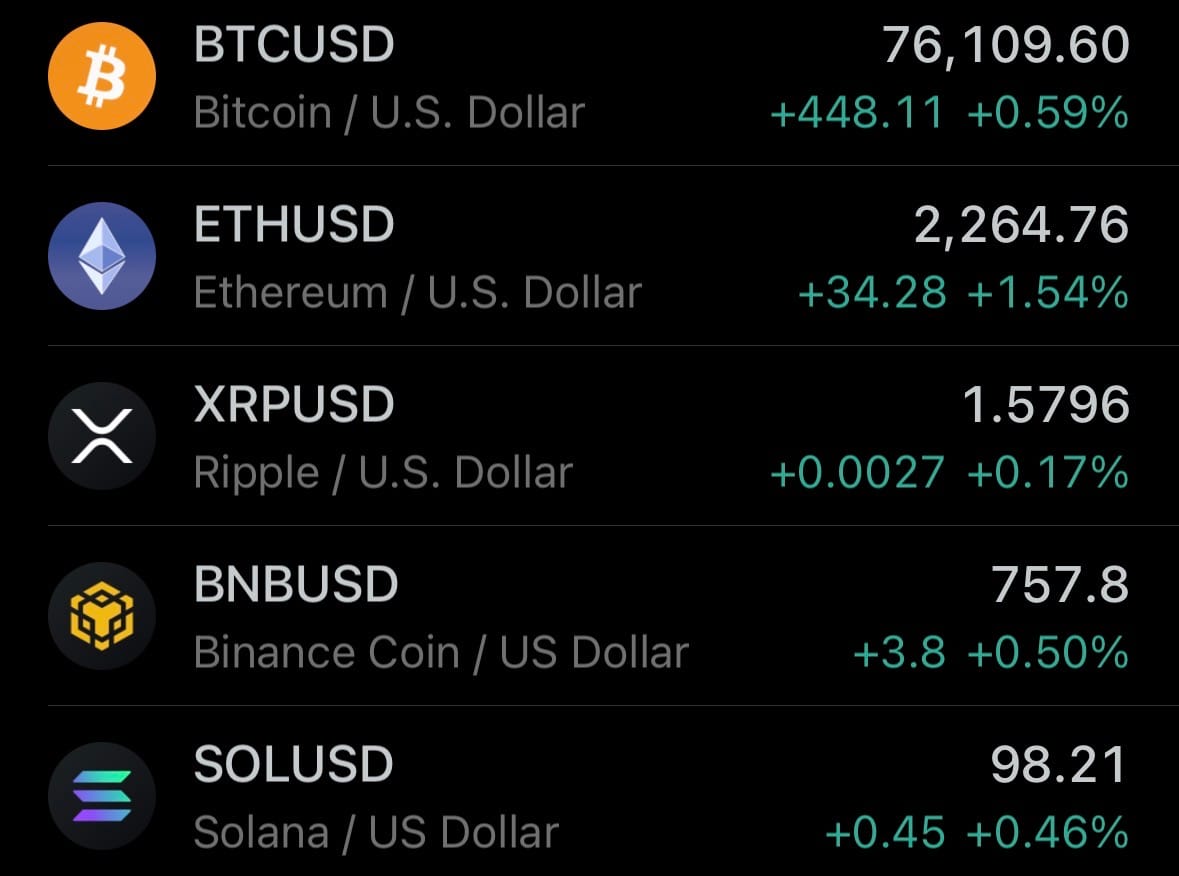
- Yesterday’s crypto market:
Geopolitics & Military Activity:
- On February 3, 2026, the U.S. military shot down an Iranian Shahed-139 surveillance drone in the Arabian Sea after it aggressively approached the USS Abraham Lincoln (CVN-72) Carrier Strike Group. According to U.S. officials, an F-35C Lightning II from Marine Fighter Attack Squadron 314 (VMFA-314), embarked on the carrier, engaged and destroyed the drone.
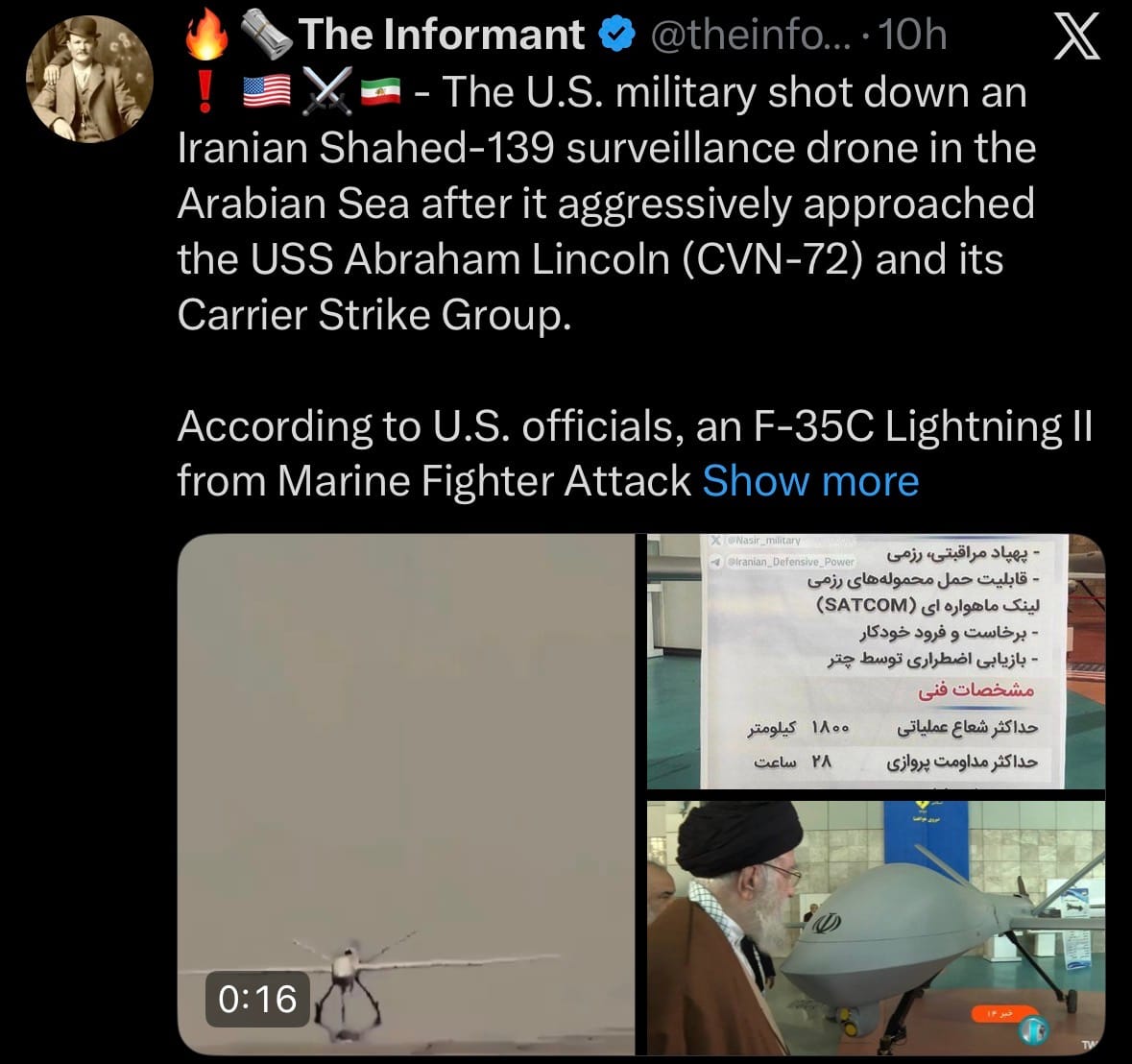
- The incident occurred in international waters, with no damage or injuries reported to U.S. ships or personnel. The U.S. described the drone's approach as provocative and a potential threat to the strike group, consistent with heightened tensions in the region.
Environment & Weather:
- On February 3, 2026, a magnitude 6.0 earthquake struck central Myanmar at 14:47 local time (09:17 UTC). The epicenter was located about 45 km northwest of Mandalay, at a shallow depth of around 10–15 km, according to preliminary reports from the United States Geological Survey (USGS) and Myanmar's Department of Meteorology and Hydrology.
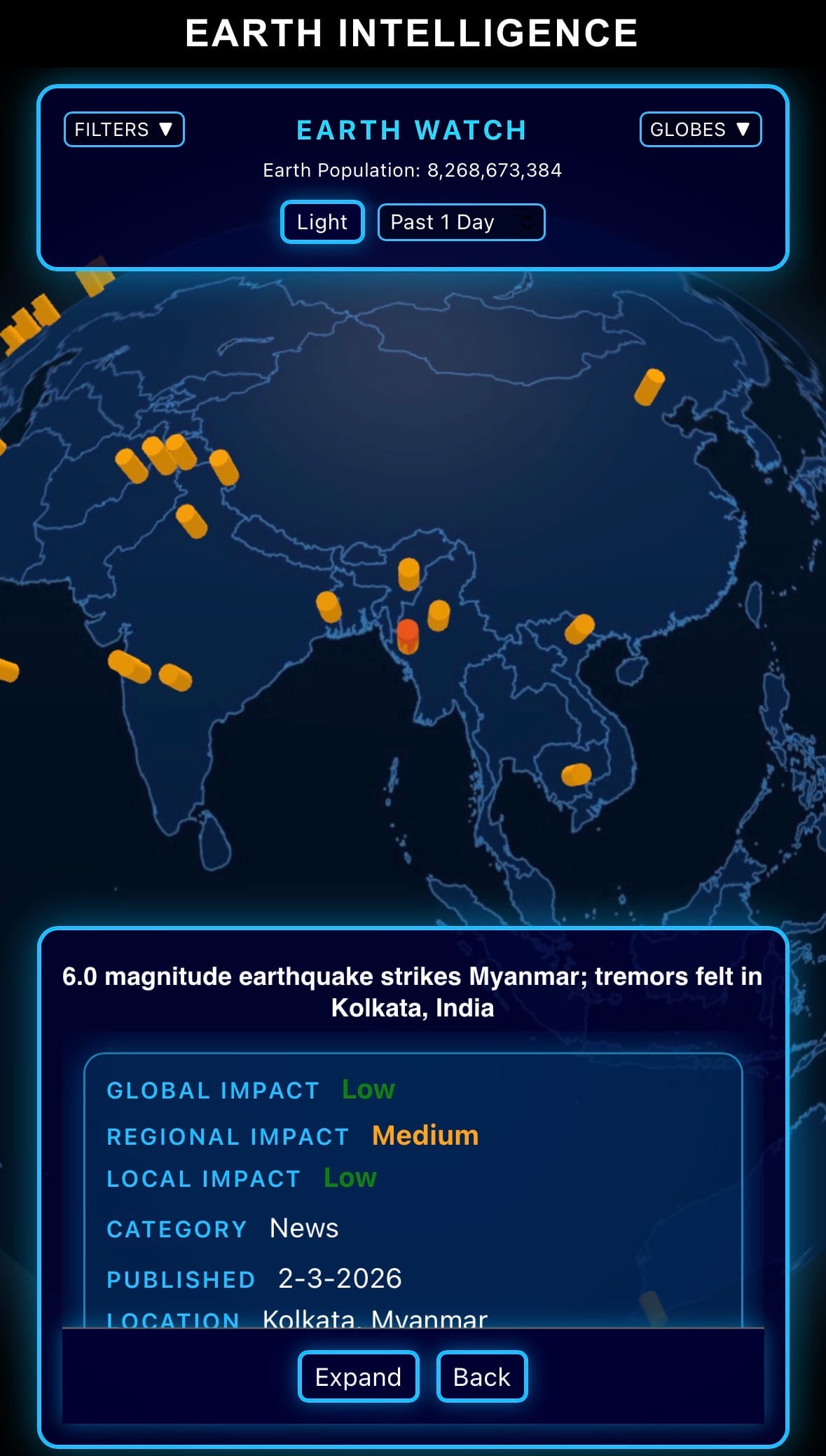
- The quake was widely felt across central Myanmar, including Mandalay, Naypyidaw, and parts of Sagaing and Magway regions. Tremors were also reported in neighboring areas, including eastern India (notably Kolkata and parts of West Bengal), northeastern Bangladesh, and southern China (Yunnan province). No immediate reports of major damage, casualties, or infrastructure collapse were confirmed, though some light shaking and minor building cracks were described in social media posts from Mandalay.
Science & Technology:
- On February 3, 2026, OpenAI announced that GPT-5.2 and GPT-5.2-Codex are now 40% faster due to optimizations in their inference stack. The update applies to all API customers and requires no changes from users. The models themselves (same weights and capabilities) deliver significantly lower latency across the board, improving response times for chat completions, function calling, agent workflows, tool use, and code generation tasks.
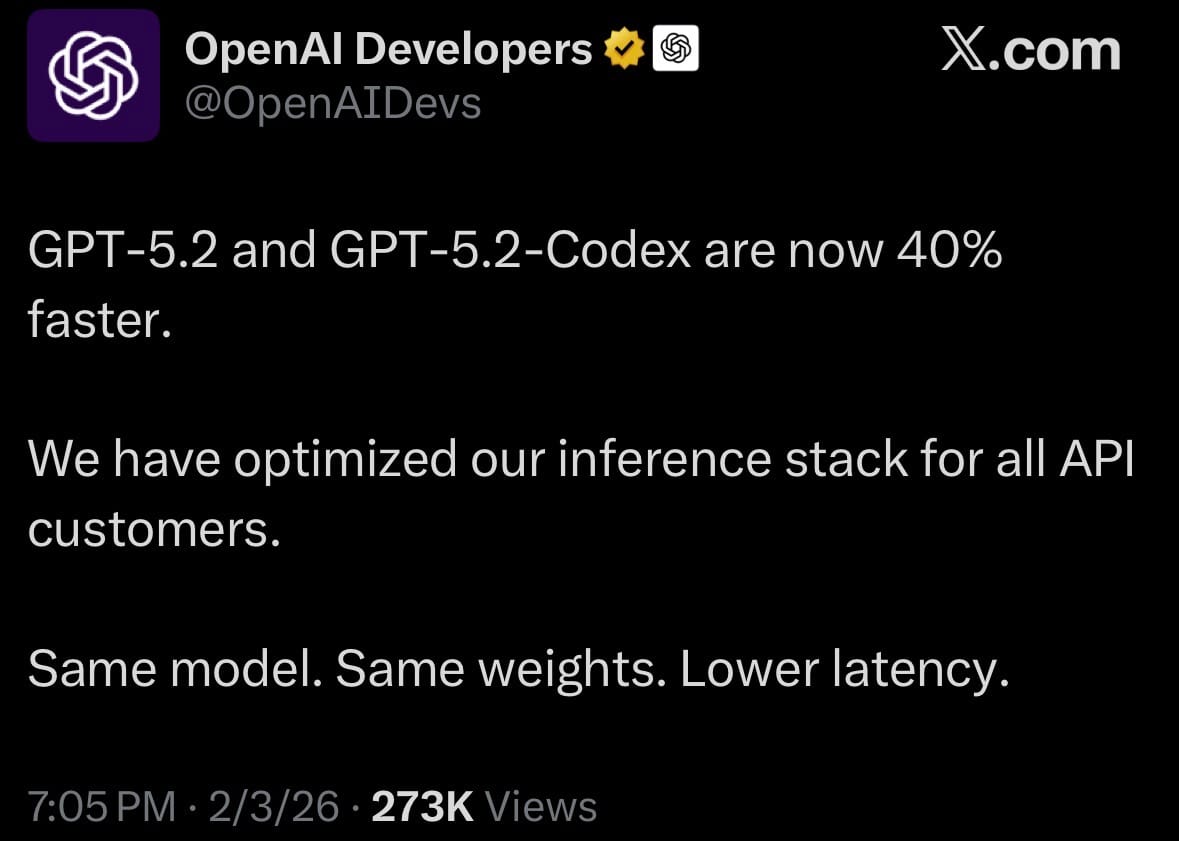
- OpenAI stated the speed boost comes from internal engineering improvements to token throughput and queuing, without sacrificing quality or increasing costs. The change is live immediately for all paid API tiers (including the new Codex app on macOS), with no downtime or migration needed. Early benchmarks shared by developers confirm noticeably quicker outputs, especially for long-context or multi-turn interactions.
Space:
- On February 3, 2026, Rocket Lab announced the company has established four dedicated facilities to enable rapid manufacturing, research and development, testing, and launch operations. These facilities are: the Neutron Production Complex in Virginia (next to Launch Complex 3 at Wallops Island) for major assembly and production; the Middle River, Maryland site for carbon composite structures and automated manufacturing; Long Beach, California for Archimedes engine development and testing; and NASA’s Stennis Space Center in Mississippi for engine qualification firings.

- This infrastructure supports fast iteration (including ongoing Stage 1 tank production) and positions Neutron for multiple launches starting in 2026 from the dedicated LC-3 pad in Virginia, emphasizing reusability and high-cadence payload delivery.
Statistic:
- Largest public banks by market capitalization:
- 🇺🇸 JPMorgan Chase: $857.10B
- 🇺🇸 Bank of America: $397.62B
- 🇨🇳 ICBC: $370.06B
- 🇨🇳 Agricultural Bank of China: $335.99B
- 🇨🇳 China Construction Bank: $329.20B
- 🇬🇧 HSBC: $305.48B
- 🇺🇸 Morgan Stanley: $290.70B
- 🇺🇸 Wells Fargo: $289.76B
- 🇺🇸 Goldman Sachs: $284.25B
- 🇨🇳 Bank of China: $247.56B
- 🇨🇦 Royal Bank of Canada: $239.62B
- 🇺🇸 Citigroup: $210.61B
- 🇯🇵 Mitsubishi UFJ Financial: $209.49B
- 🇺🇸 Charles Schwab: $188.29B
- 🇦🇺 Commonwealth Bank: $181.18B
- 🇪🇸 Santander: $180.85B
- 🇮🇳 HDFC Bank: $172.19B
- 🇨🇦 Toronto Dominion Bank: $160.84B
- 🇨🇳 CM Bank: $153.92B
- 🇨🇭 UBS: $150.21B
- 🇪🇸 Banco Bilbao Vizcaya Argentaria: $145.80B
- 🇺🇸 Capital One: $141.98B
- 🇮🇹 UniCredit: $135.92B
- 🇯🇵 Sumitomo Mitsui Financial Group: $135.75B
- 🇸🇬 DBS Group: $132.27B
History:
- Encryption begins the moment writing becomes valuable enough to protect. In the ancient world, secrecy was achieved through obscurity rather than mathematics. Mesopotamian scribes (c. 2000 BC) hid trade secrets by altering symbols; Egyptians embedded nonstandard hieroglyphs into inscriptions; Spartans used the scytale—a physical transposition device—to send military orders; and Rome, by the 1st century BC, formalized substitution with the Caesar cipher, shifting letters to conceal battlefield commands. These early methods assumed low literacy and slow interception. As states grew more complex, cryptography followed. Medieval and Renaissance powers relied on codebooks, nomenclators, and cipher alphabets, especially in diplomacy, espionage, and court intrigue. By the 16th–18th centuries, European states maintained permanent cryptographic offices, and codebreaking became a formal intelligence discipline—patterns, frequency analysis, and intercepted correspondence deciding alliances, assassinations, and wars. Encryption at this stage was manual, fragile, and human-scaled, but it established a permanent truth: secrecy and power rise together, and every cipher invites a breaker.
- The industrial and mechanical age transformed encryption from clever tricks into engineered systems. The telegraph and radio in the 19th and early 20th centuries made interception easy and unavoidable, forcing cryptography to scale in complexity and speed. This culminated in World War I and World War II, when encryption became decisive to national survival. Mechanical cipher machines automated complexity—rotors, wiring, and keys producing astronomical combinations. Germany’s Enigma and Lorenz machines epitomized this era, while Allied cryptanalysis—combining mathematics, intelligence, and early computing—proved that encryption strength depended not just on algorithms, but on key management, discipline, and operational security. After WWII, cryptography became permanently institutionalized. During the Cold War, encryption underpinned nuclear command-and-control, satellite communications, intelligence traffic, and secure diplomacy. Governments treated strong cryptography as a weapon, tightly controlling its export and development. This era also produced the first formal encryption standards designed for computers. In the 1970s, the Data Encryption Standard (DES) emerged as a widely adopted symmetric cipher, later replaced by Advanced Encryption Standard (AES) in 2001, which remains the global standard for securing data at rest and in motion.
- The digital era turned encryption into global infrastructure, and mathematics replaced secrecy-by-obscurity forever. The breakthrough was public-key cryptography in the 1970s, which solved the key distribution problem and enabled secure communication between strangers. Systems like RSA and later Elliptic Curve Cryptography (ECC) made digital signatures, secure key exchange, and identity verification possible at planetary scale. These techniques power modern standards such as TLS (securing the web), PKI (digital certificates and trust chains), and cryptographic hash functions like SHA-256, which ensure integrity across software, finance, and distributed systems. Encryption now secures smartphones, cloud platforms, military networks, satellites, identity systems, and digital currencies. Today, the field faces its next inflection point: quantum computing. Large quantum machines could break many classical public-key systems, driving a transition to quantum-safe (post-quantum) cryptography based on new mathematical foundations—most notably lattice-based systems like CRYSTALS-Kyber (key exchange) and CRYSTALS-Dilithium (digital signatures), along with hash-based schemes designed to resist quantum attacks. Modern encryption is no longer just about secrecy—it is about trust across time, ensuring that data intercepted today remains secure decades into the future. From clay tablets to quantum-safe algorithms, cryptography has evolved into one of the most decisive technologies of civilization, because it governs who can communicate privately, who can be trusted, and which systems will obey in a world where information is power.
Image of the day:

Thanks for reading! Earth is complicated, we make it simple.
- Click below if you’d like to view our free EARTH WATCH globe:
- Download our mobile app:


Click below to view our previous newsletters:

Support/Suggestions Email:
earthintelligence@earthintel.news




